RED HAWK: Multiple Scanning And Attack Vector
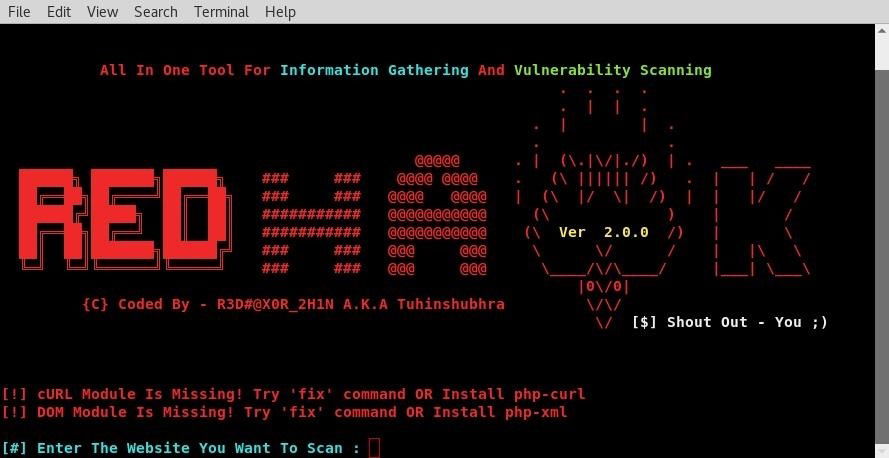
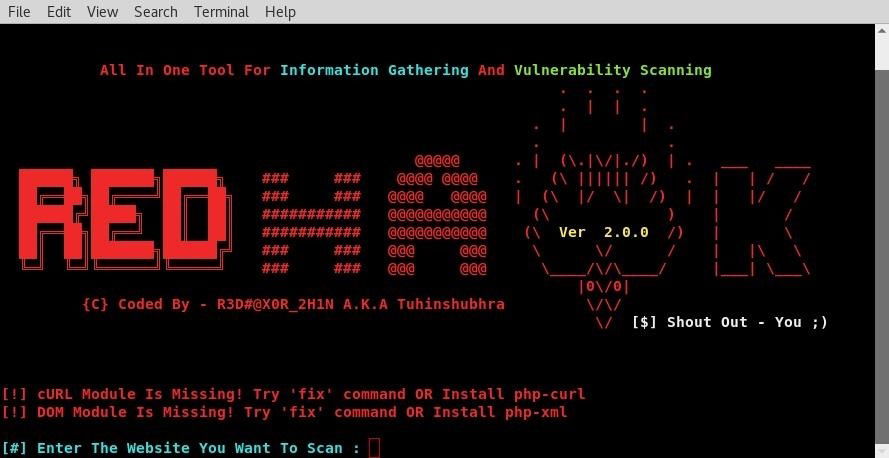
Hello friends, so today we are going to know about a tool RED HAWK, which can be used to gather some information regarding a target and determine some crucial information regarding the hosting information of the company, location, protocols used etc…… these come under Information gathering. It is the most crucial part for any hacker or pentester to perform a hack or simulate a hack. Information gathering mainly consist of
- Network architecture
- Connected devices
- Open ports
- Running services
- Known vulnerabilities
- Password profiling,etc……
There are many information gathering tools available over GitHub and over the internet out of that many ones is RED HAWK
RED HAWK is one of Best Information gathering tool written in PHP.it’s an all in one tool capable of gathering like Information Gathering (using WHOIS lookup, WordPress, Reverse IP Scanner etc.), SQL Vulnerability Scanning and Crawling.
to know more about information gathering visit this page Information Gathering
Features Of The Tool:
- Server detection
- CloudFlare detector
- robots scanner
- CMS Detector
- WordPress
- Joomla
- Drupal
- Magento
- Whois
- GEO-IP Scan
- NMAP Port Scan
- DNS Lookup
- SubNet Calculator
- Subdomain Finder
- Reverse IP Scanner
- CMS detection For Sites On the same server.
- Parameter Finder
- Error based SQLi Detector
- Crawler
- Basic Crawler {69}
- [ – ] Admin scanner
- [ – ] Backups Finder
- [ – ] Misc. Crawler
- Advance Crawler{420}
- [ – ] Admin scanner
- [ – ] Backups Finder
- [ – ] Misc. Crawler
To access RED HAWK we need to clone it from Github or download the zip file from GitHub
The Installation:
- Open up a terminal and type in “git clone https://github.com/Tuhinshubhra/RED_HAWK.git”
This will attempt to clone the git repository and will place all the files in the repository into a directory named RED_HAWK of you working directory.
If you have downloaded zip then just extract it and open a terminal in the extracted folder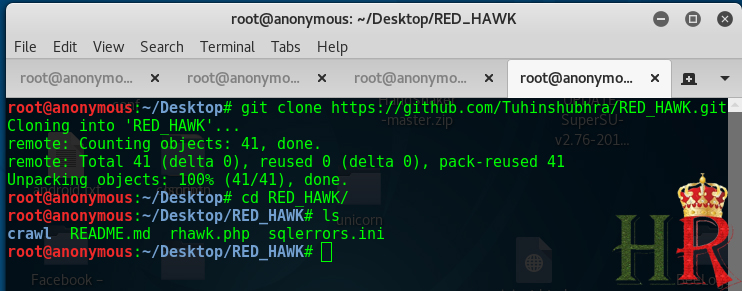
- Now change you directly to the RED_HAWK folder using the command “cd RED_HAWK”
- We can list the available files in the folder using the ‘ls’ command. To run the RED HAWK type in “php rhawk.php”.
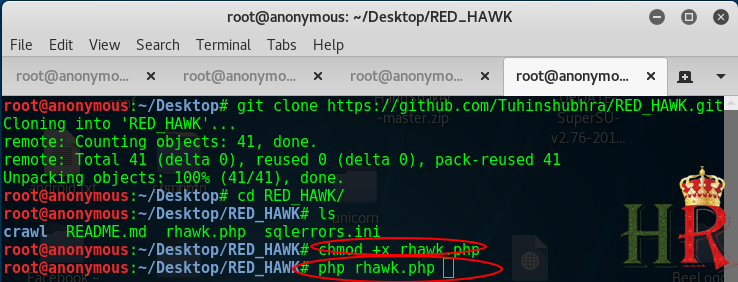
- You will get the RED HAWK interface. Type “help” to list the available options for us
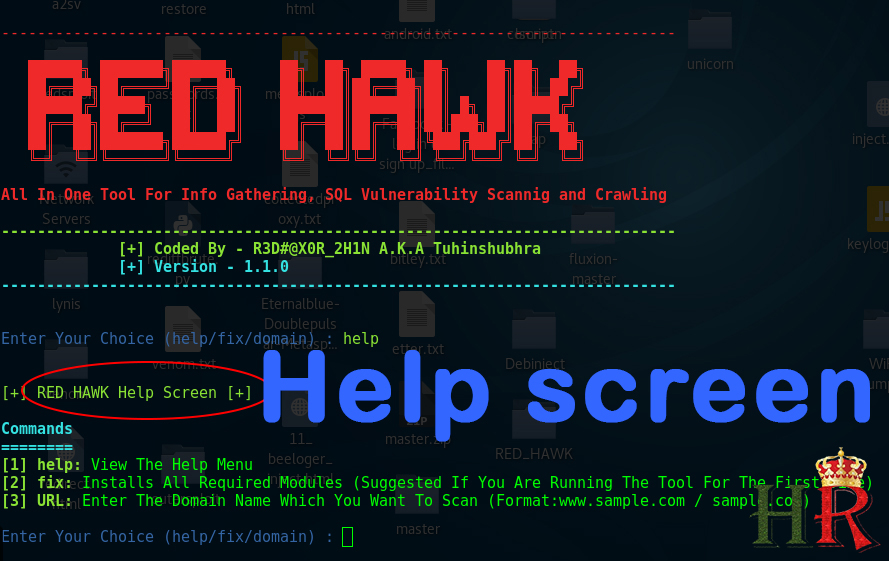 NOTE: if you face any error in the run the tool then type “fix” this will Install All Required Modules.
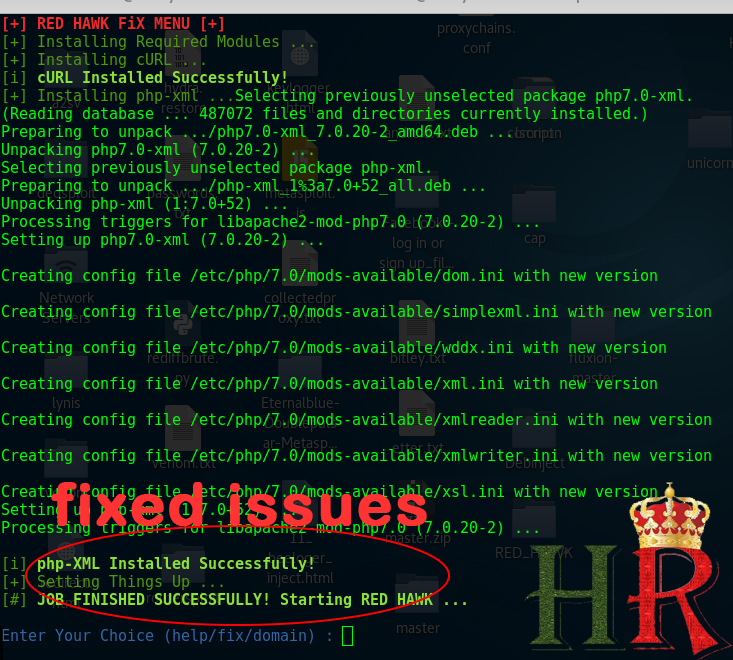
NOTE: if you face any error in the run the tool then type “fix” this will Install All Required Modules.
- Type in the domain name you want to scan (without Http:// OR Https://).for example we are setting facebook.com as a target.
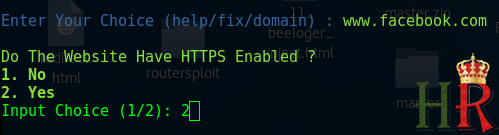
- Select whether The Site Runs On HTTPS or not. If it does it is preferred to select HTTPS for better scanning and results.
NOTE: if Scanner Stops Working After CloudFlare Detection! Use The fix Command OR Manually Install php-curl & php-xml
as seen in the below screenshot it does a nmap scan to identify services on ports and find open ports to gather information related to the operating system running, Firewall, Traceroute etc… to know more about nmap scan, please read this article All Nmap tool commands at your fingertips!
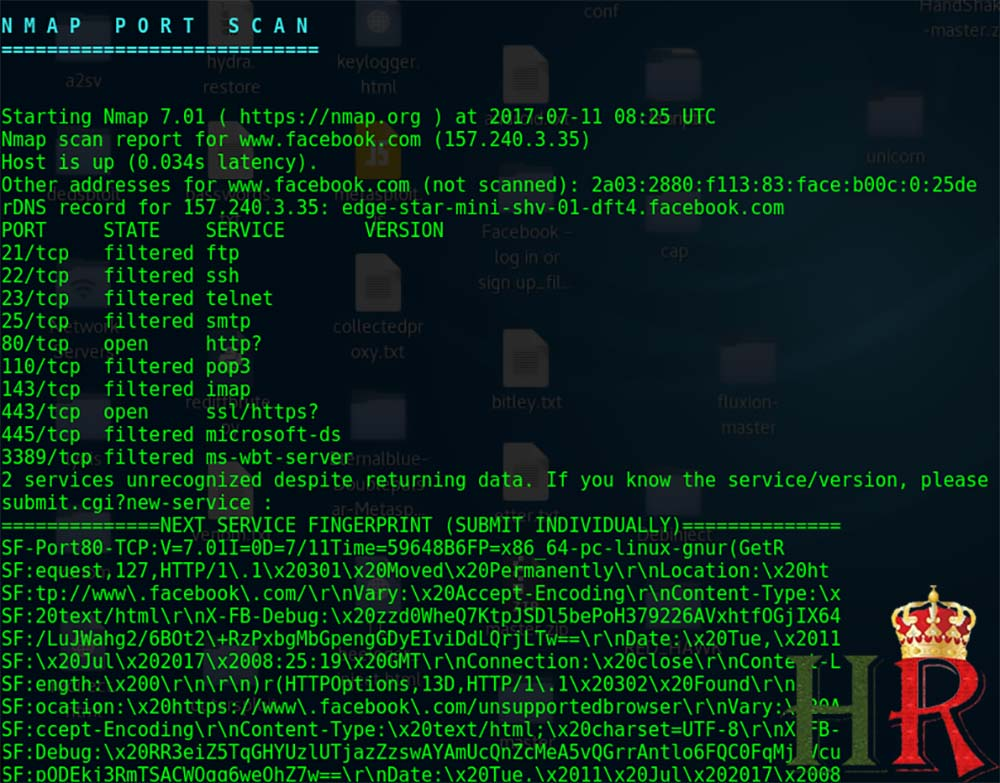
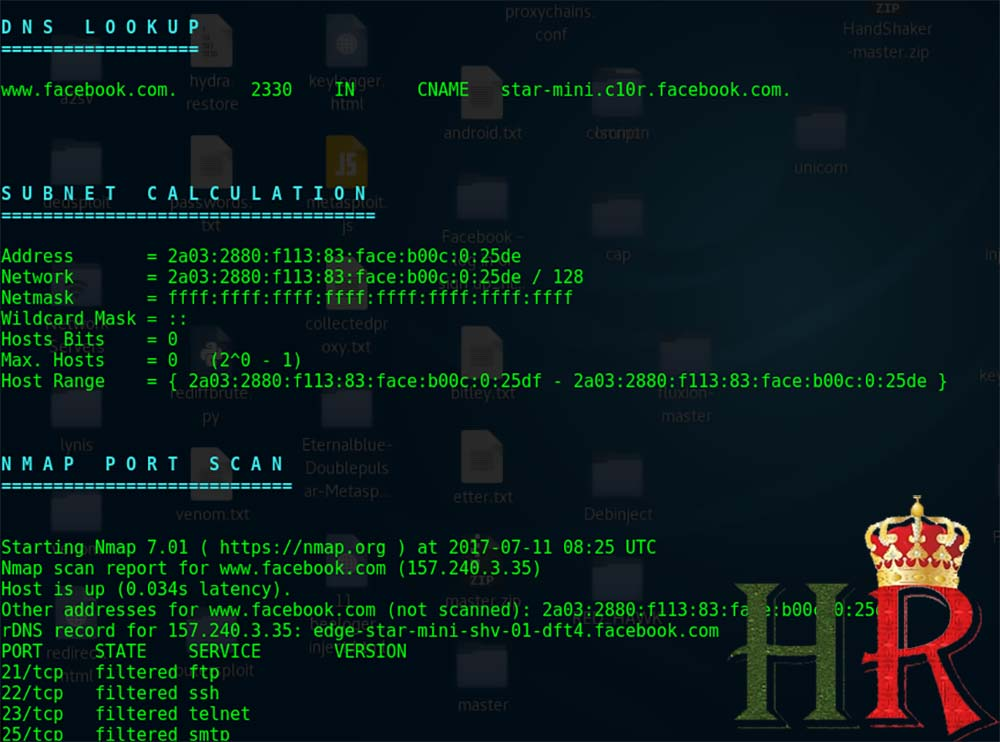
it also does a DNS scan related to our target to determine for DNS vulnerabilities and display the subnet available for the target we selected, as we can see that we get information regarding that Facebook usesIPv6 protocol
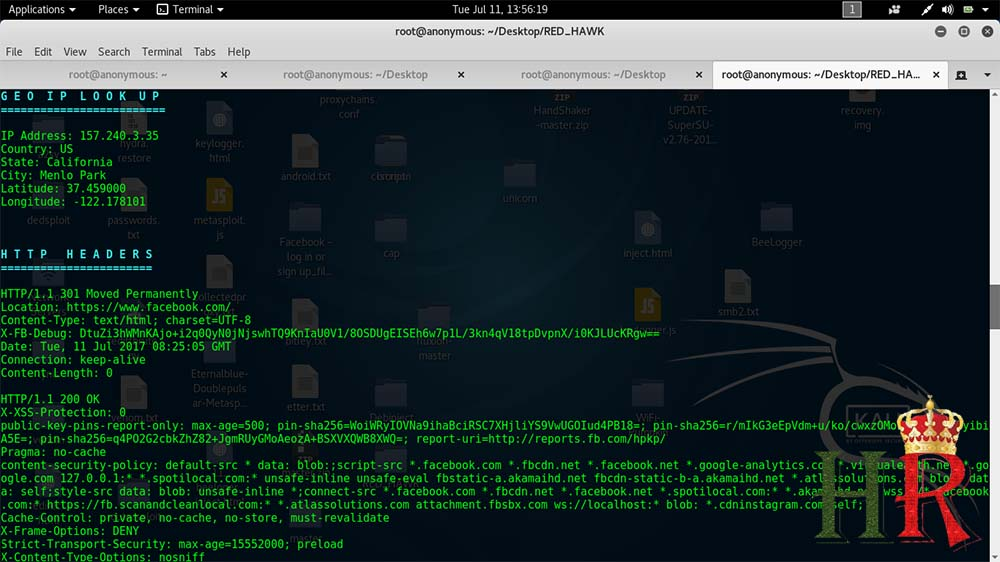
this tool also determines the geographical location of our target similar to the results of shodan, to know about shodan read this article on How To Use Shodan For Finding Vulnerable Targets, Information Gathering & Hacking?
as mentioned this tool does more than we can imagine. this tool does our work more easy by automating all the required tasks of Information gathering, taking each and every single point of interest regarding our target.
hope you had enjoyed reading this article if you did kindly share to let your hacker friend(s) know that there is a tool which can let his/her work of information gathering more simple and easy giving him/her a plenty of time to plan the attack. If you have any queries regarding the article then do comment below and let us know how you felt reading the article. Thank You.
