Unistellar Attackers Delete Over 12,000 Unsecured MongoDB Databases


With around 12,000 unsecured MongoDB databases being deleted in the course of three weeks, attackers have solicited the owners from the databases to contact the said cyber-exotortionists to have the information restored with just a message left behind.
They search for the already exposed database servers utilizing BinaryEdge or Shodan search engines, delete them and demand a ransom for their 'restoration services' and these sorts of attacks focusing on the publicly available MongoDB databases have known to have occurred since atleast the early 2017 [1, 2, 3, 4].
While Mongo Lock attacks likewise target remotely open and unprotected MongoDB databases, the campaign does not appear to demand a particular ransom. Rather, an email contact is given, well on the way to arrange the terms of information recuperation.
Sanyam Jain, an independent security researcher and the person who found the wiped out databases, gave quite a sensible clarification to this, saying that "this person might be charging money in cryptocurrency according to the sensitiveness of the database."
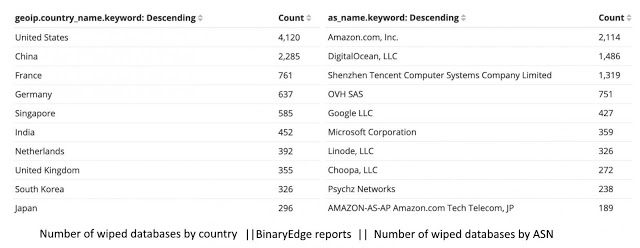
The 12,564 unprotected MongoDB databases wiped out by Unistellar were found by the researchers utilizing BinaryEdge. Seeing that, right now, BinaryEdge indexes somewhat more than 63,000 publicly accessible MongoDB servers as per Jain, it appears as though the Unistellar attackers have dropped by approx 20% of the aggregate.
The cyber-extortionists leave behind notes asking their victims to connect with them if they need to reestablish their data by sending an email to one of the accompanying two email addresses: unistellar@hotmail.com or unistellar@yandex.com.
Shockingly, there is no real way to follow if their victims have been paying for the databases to be reestablished on the grounds that Unistellar just gives an email to be reached and no cryptocurrency address is given.
These attacks can happen simply because the MongoDB databases are remotely open and access to them isn't appropriately verified. This implies that the database owners can without much of a stretch forestall such attacks by following genuinely basic steps intended to appropriately secure their database instances.
MongoDB gives details on the most proficient method on how to verify a MongoDB database by actualizing legitimate confirmation, access control, and encryption, and furthermore offers a security agenda for executives to pursue.
More to the point, significant measures will undoubtedly be taken which will additionally forestall the attacks by empowering authentication and to not enable the databases to be remotely accessible.
